Mobile Penetration Testing

Using a combination of manual and dynamic analysis and testing along with custom automated fuzzing, Dynamics Technologies’s Mobile Security Testing covers areas such as:
Storage protection
Transport protection
Authentication
Authorization
Cryptography
Session management
Data validation
Error and exception handling
For open mobile platforms such as Android, mobile applications are also decompiled to maximize understanding and testing coverage. For closed platforms such as iOS, source code is often requested to accompany the engagement or binaries can be reversed at runtime.
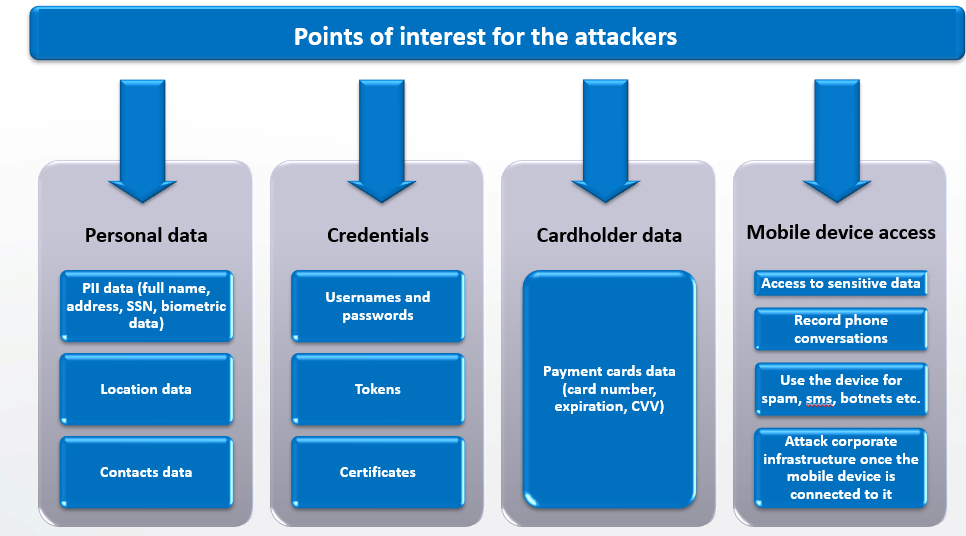
Our engineers begin the assessment by evaluating data protection controls on the client device. In particular, the engineers will examine where and how the application manages sensitive information, whether the application is properly utilizing native APIs for features like key stores, and whether dangerous client artefacts such as user credentials, personal information or any other sensitive application data is unintentionally or insecurely stored on the phone.
Application package analysis
Reverse engineering
Static analysis
Dynamic analysis
File system analysis
Inter-Process Communication Endpoint Analysis
Content providers
Intents
Broadcast receivers
Activities
Services
Using commercial, open source, and proprietary tools, SafeByte implements a structured testing methodology based on OWASP’s Mobile Security Testing Guide (MSTG) to make the mobile application assessment as efficient as possible. During the testing, we simulate a multitude of attacks, both general application attacks and mobile dedicated attacks. The testing simulates a real hacker and what he can do to penetrate the application and retrieve confidential information.
